How Cyber Attacks Outsmart the Gaming World
Regulations, Scale and the Human Element
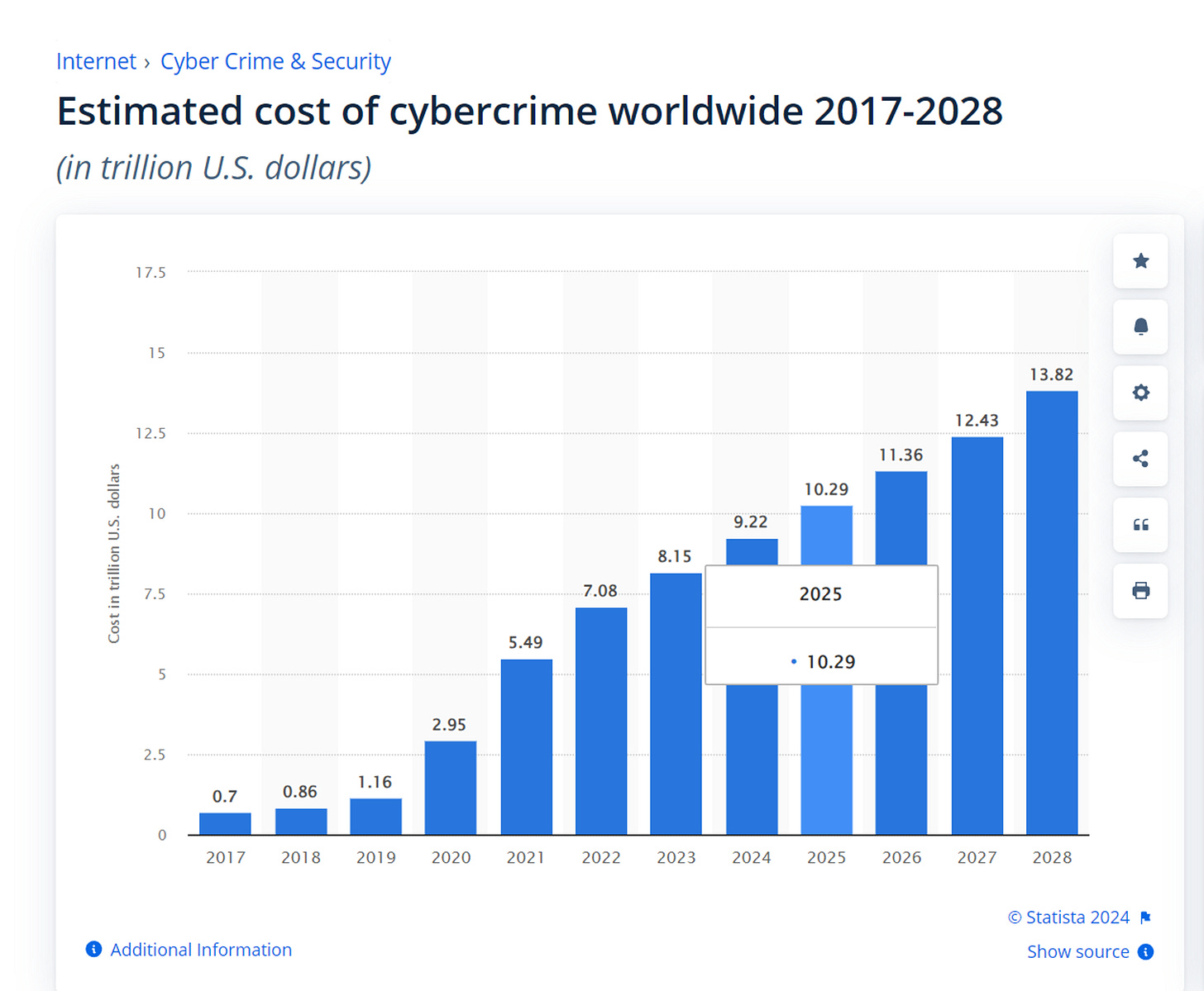
$10.5 Trillion USD in Global Cybercrime Damage Costs
The Games Industry: The Largest Unregulated Financial Market
Top 3 Reasons for Inadequate Cybersecurity
…That's $18 Million a minute, $800 Billion a month and $10.5 trillion a year.
That will be the damage cost of global cybercrime in 2025, with the gaming industry squarely in the crosshairs. Working in gaming myself, I was curious why big game companies still can’t properly fend off hacker attacks. Turns out, the reasons are both complex and straightforward.
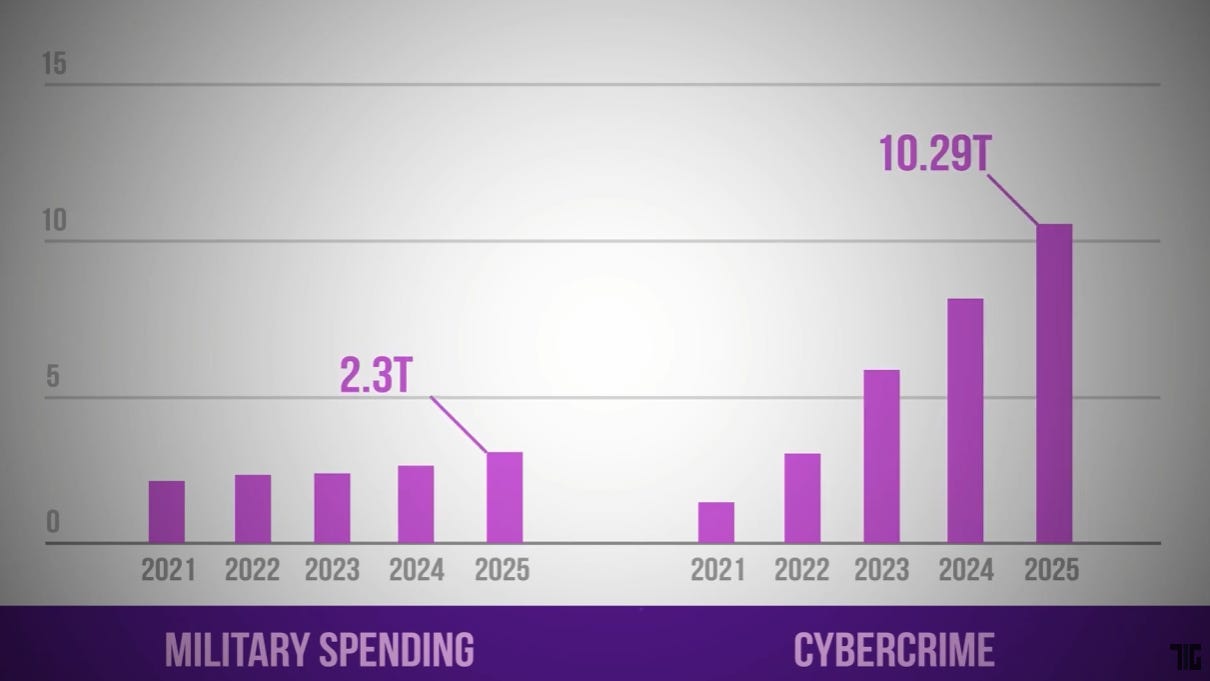
Cybercrime has become an epidemic. If measured as a country, then cybercrime would be the world’s third-largest economy after the U.S. and China. That’s four times more than global military spending.
A virus that’s alread winning big time: It’s larger than the yearly natural disaster costs and will be more profitable than the entire global illegal drug trade combined. It’s the biggest wallet drain in history. Manufacturing and finance are attacked the most but the biggest attack was in the healthcare sector with WannaCry by alleged North Korea's Lazarus Group. They hit 150 countries, infected over 200,000+ computers, and stole $625 million in cryptocurrencies. Recovery cost? $4 billion USD.
And the games industry? Well, it’s under siege. Because ever since the pandemic hit, gaming’s traffic spiked with game downloads of over 300 Terabytes per second. That’s like watching 50.000 movies simultaenously, every second. That’s a loooot of data traffic. And looking at this beautiful map here, the countries with highest rate of cybercrime are Russia, followed by Brazil, the US, China and Germany. It’s a worldwide issue. No kidding. and the latest news really read like a wake-up call:
Ubisoft targeted by hackers…AGAIN!
“Hackers breach Electronic Arts,” “Insomniac Games targeted in hack,” “Hackers took over dev accounts on Steam,” “Sony at the verge of major leak", “Activision suffers data breach,” “CoD plans stolen,”…but wait, it gets better: “Hacking Gang Claims to Have Stolen 200 GB of Epic Game's Data” only to then admit that it was all made up and a total scam.
“We don't think of ourselves as hackers but rather as criminal geniuses, if you can call us that.”
Mogilevich hacking group
If THAT’s genius, what would that make me…?
I don’t know, but what I do know is that while the last one was a scam, the goal across the board is the same: MONEY. Most folks think hackers attack game companies just to leak the next big title for kicks; but nope. It’s really just for the cash.
And with $180.0 billion in revenue, gaming is booming, which is indeed catnip for cybercriminals. You know how much revenue game companies made just from total game sales?
Minecraft: $3B
Apex Legends: $2B
Fortnite: $26B
Roblox: $9B
GTA 5: $8B
GTA 5 Online: $800m/year from in-app purchases.
You see; Game companies aren’t just game companies anymore - they are major financial targets. With huge amounts of customer data and financial transactions. Just look where the microtransaction market is heading: $100 Billion by 2026. And the shift to subscription models means even more personal data up for grabs.
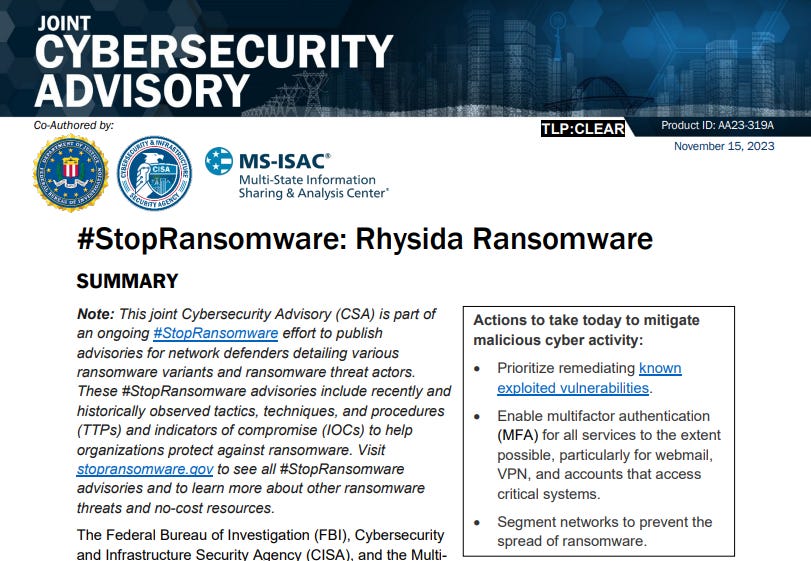
Ever heard of the hacker gang Rhysida? I didn’t, but check this out:
That’s the same gang behind the Insomniac Games leak from last year. When they hacked the studio they demanded 50 Bitcoins ($2 million) for over 1.3 million files, including unreleased Wolverine game footage. Their motivation?
”We knew that devs making games like this would be an easy target. Our motivation is money.”
They are so famous that even the US Department of Justice had to step in, asking everyone to please enable MFA.
This becomes even more important as we are moving to all things cloud and mobile. That’s a double-edge sword. The cloud’s centralized, advanced security makes hacking tough. But if hackers get in, they hit a jackpot with data from multiple companies. And with more of us working from home, there's even more stuff going through the cloud. When hackers leaked GTA 6 footage, Rockstar Games asked their workers to come back to office 5 days a week. All for security reasons.
And I get that. Because in next year, we’re gonna have a whopping 200 zettabytes of data stored EVERYWHERE - across all devices. Do you know how much 200 zettabytes of data are? I didn’t, but I googled. It’s like stacking smartphones from Earth to the Sun and back over 100 times. That’s a gold mine for hackers. Especially now that we have 5B people online. And guess how many of those are gamers? That’s right. More than half. More cloud, more devices, more gamers…means what? A much larger attack surface for hackers.
And how do they attack? There are many tactics - or so called Attack Vectors - but the top three are:
DDOS attacks, hackers overwhelm servers with requests so much so they slow down the service or shut it down altogether. The games industry is plagued by relentless DDoS attacks, targeting companies big and small. Riot Games - perfect example. They have a whole catalogue of DDoS attacks over the years, mostly bringing down their League of Legends servers. Besides the cyberattack in 2023, when the games source code was stolen, the latest one happened just a few days ago. The LCK faced a cyber-attack where servers suffered persistent DDoS attacks causing the matches to be delayed and eventually rescheduled. (B-roll) The network delays were so many, players sneaked in some sleep as the event stretched to a record 7 hours!
And then there’s Ransomware, which is everywhere. With Ransomware-as-a-Service - yep, that exists - attackers use phishing emails and compromised credentials to find vulnerabilities. Once inside, they deploy ransomware to encrypt the data, demanding a ransom for decryption keys. The idea that people could buy ransomware the same way they buy other software…it’s fascinating.
CDPR experienced a huge ransomware attack when hackers obtained the source code for Cyberpunk 2077, The Witcher 3 and Gwent, with a 48h ultimatum.
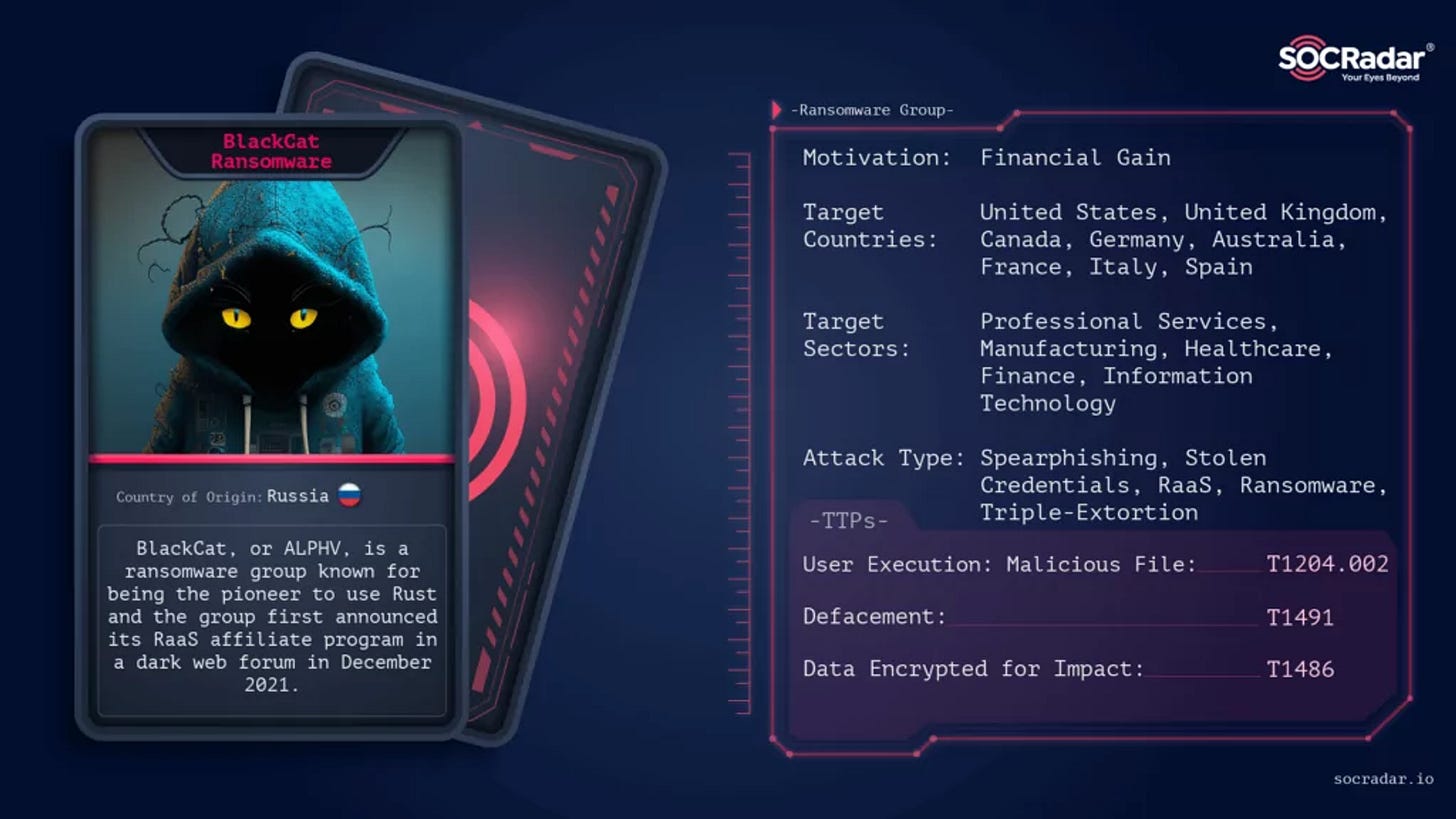
Bandai Namco also suffered a ransomware attack in 2022 by the BlackCat group, obtaining corporate and customer information. And only after the attack did Bandai promise to strengthen their security system.
(BlackCat is interesting. They are a ransomware group that has its own RaaS affiliate program, a ransomware executable and a searchable database of stolen data! There is nothing that does not exists. No surprise that the FBI’s Cyber Division published a flash warning stating that BlackCat breached at least 60 entities worldwide. I also read that in 2031 ransomware will strike every 2 seconds, costing us $265 B a year. All I will say is: #noinvestmentadvice)
But one of the most effective tactics are social engineering attacks. That’s why hackers don’t need your password to hack. All they need to do is convince an under-informed confused person to do what they say. In the form of phishing or impersionation they trick you into revealing sensitive information. Just check this out: Then 18 yo Arion Kurtai, member of the Lapsus$ group and going by the handle “Teapotuberhacker”, hacked Uber and Nvidia before hacking Rockstar Games. With Uber, he fooled an employee by flooding him with push auth for over an hour, then messaged on WhatsApp as Uber IT. The employee accepted and Arion could add his device. He got bailed but that didn’t stop Mr. Teapotuberhacker from hacking. Apparently, all you need is an Amazon fire stick, a phone and a hotel TV. While under police protection in a hotel, he gained access to Rockstar’s Slack and obtained 90 clips of unreleased GTA 6 and the GTA 5 source code which was shared as proof that he had stolen the data. And the GTA 6 footage? Well, he did say on Slack that he’s not a Rockstar employee and that if they don’t contact him within 24 hours he will release the source code. Which…he did.
98% of cyber attacks are social engineering attacks. The consequences? Not good. Not good. From losing user trust, financial losses to reputational damage, it’s crazy.
In Insomniac’s case, the leak spilled Wolverine footage, a 12-year release roadmap, their budget for Spider-Man 3, financial details, Slack conversations, employee passport scans, and more, impacting over 400 employees. Insomniac tweeted about the emotional toll it’s taken on their dev team, and garnered loooots of support from fans and game studios alike.
When CDPR got hacked, their stock value dropped. While the stock dropped by 8% post game launch, it did drop again after the attack. And as CDPR refused to pay the ransom, HelloKitty, the hacker gang, auctioned it off on the dark web for $7 million dollars when “an offer was received outside the forum that satifsfied them.”
And in Rockstar’s case? Well, the GTA 6 leaks cost about $5M in damages and parent company Take-Two saw their stock slightly dip by 2.3%.
What might be a good buying opportunity for some, is a nightmare for others though. Employees could face doxxing, costly marketing strategies have to be adjusted, competitors gain an edge and with every game leak, trust is shattered across partners, employees and also gamers. And btw gamers: Every year, over 4 million hack attempts target gamer accounts. Minecraft tops the list, accounting for 70% of alerts.
So with so many huge scale attacks, why can techy game companies still not fully shield themselves?
Regulations. To be precise, the lack of regulations. The games industry is one of the world's largest unregulated financial markets. Banks and hospitals have super strict cybersecruity protocols, but for gaming the rules are much looser, which means some are playing loose with cybersecurity. With all the microtransactions, things should be as strictly secured as banks. But they aren’t. So the less they’re regulated, the less they spend on security. The only few regulations they abide to are the GDPR and California’s CaCPA, both imposing huge fines, but that’s not enough to wake everyone up.
Scale & Innovation. There’s this misconception that there’s an “end” to cybersecurity. There never is. The larger the company, the more complex the systems, the more vulnerabilities there are. Also, game companies adopt new technologies faster than other sectors, which means the proper security protocols are not yet in place. It’s always a race between new tech and missing protocols.
But the biggest issue, is us. Even with fancy tech, it’s the staff, the contractors, the partners, the gamers that are the weakest link in the security chain. That’s why social engineering attacks are so effective. There is a reason that cybersec company KnowBe4 is worth $4.6B. There’s a general lack of cybersecurity awareness.
I’m guilty myself - I don’t renew my passwords as often as I should, I skip multi-factor-authentication because I’m lazy. Without MFA, it’s a child's play for hackers. It's like stealing candy from a baby— only that in this case the baby is a multi-billion dollar industry.
So what can we do about it?
Well, for once, I myself shouldn’t be so lazy and set up MFA wherever possible, renew my passwords, keep software updated and make sure others do the same.
On a company level, well, they need to step up their game and start thinking about security right from the start when a game is being developed. Not post hacker attack.
There should be mandatory awareness training for employees and gamers alike. In our remote work world some companies do realize that and adopted a so called zero-trust approach, which means “trust no one, verify everyone”, whether at home or in the office.
It can be annoying to always having to verify yourself, but in the world of cybersecurity, the greatest threat isn’t code or a system bug, it’s something much harder to remediate - and that’s the human element.